
Cybersecurity Solutions
Emdad CCS delivers end-to-end cybersecurity, networking, cloud, and computing infrastructure solutions designed to empower organizations in their digital transformation.
Cybersecurity Services
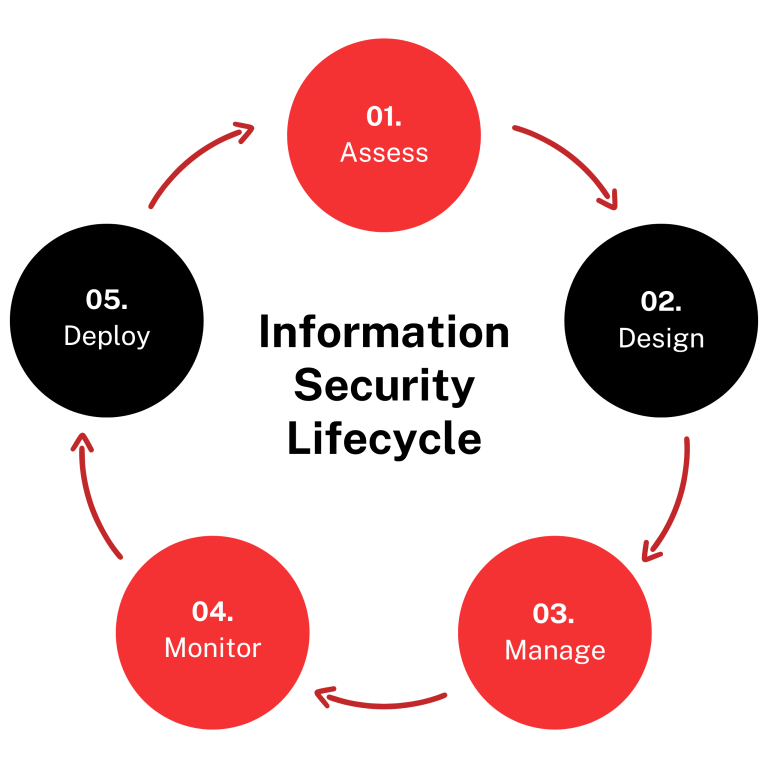
Information Security
Data Security
Network Security
Cybersecurity Services
Protect your business with end-to-end security and compliance solutions:
Information Security
Protect sensitive business information by implementing strict access, monitoring, and policy controls.
- Data classification and labeling: Ensure data is tagged and handled based on sensitivity (e.g., confidential, internal, public).
- Insider threat detection: Monitor user behavior and system access to identify potential malicious or negligent actions.
- Policy enforcement and logging: Enforce access policies while maintaining comprehensive logs for accountability and audit readiness.
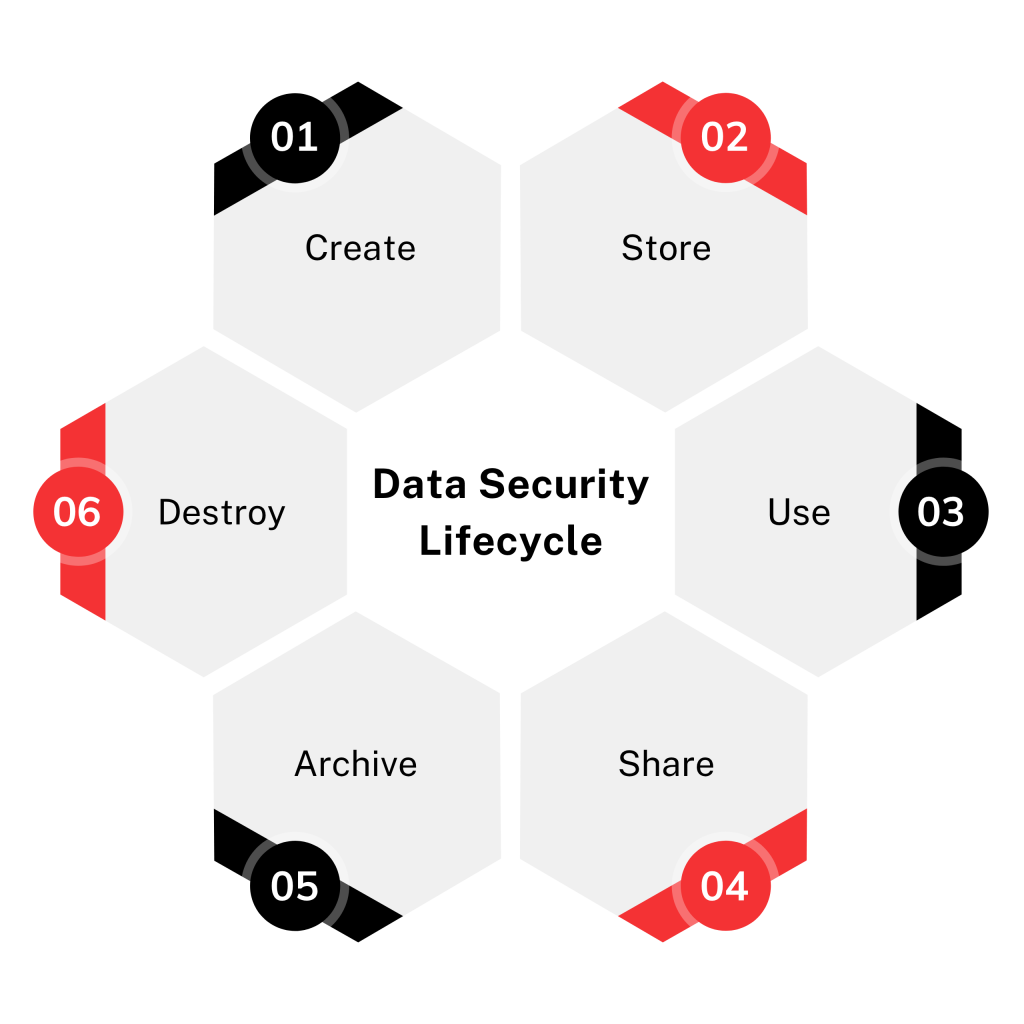
Data Security
Secure your data at rest, in motion, and in use with layered protection techniques.
- DLP Implementation – Email, endpoints, network: Prevent unauthorized data transfers across email, endpoints, and network channels.
- Encryption Solutions – File-level, disk, and database encryption (AES-256, RSA)
- Data Masking & Tokenization: Obscure sensitive data using dynamic masking and tokenization to protect privacy and comply with regulations.

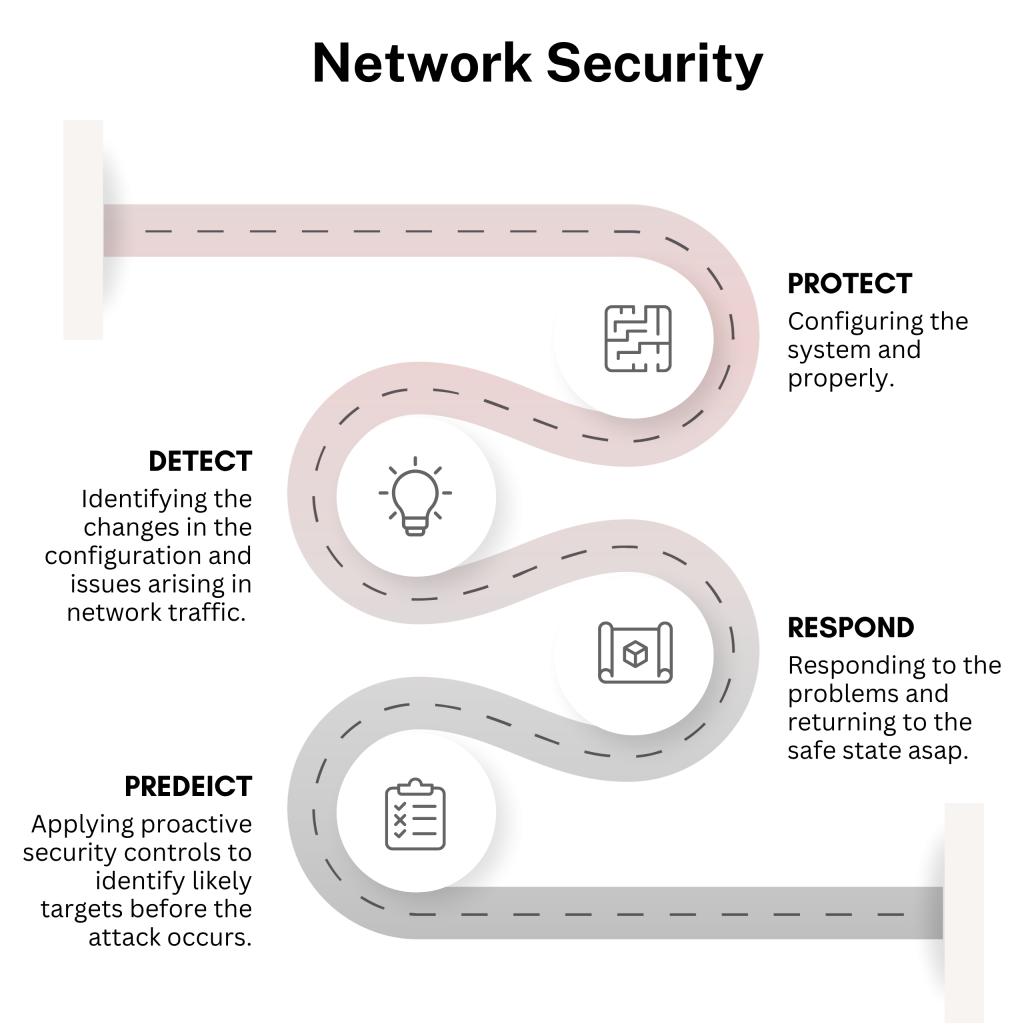
Network Security
Defend your infrastructure with intelligent perimeter, segmentation, and access controls.
- Next-Gen Firewalls & UTM: Deploy firewalls with deep packet inspection, intrusion prevention, and application-layer filtering.
- Zero Trust Architecture: Adopt a “never trust, always verify” model enforcing user, device, and application-level access validation.
- Micro-Segmentation & NAC Solutions (e.g., Cisco ISE, FortiNAC): Implement VLANs and solutions like Cisco ISE or FortiNAC to control access based on device and identity context.
Key Vendors

















